File list download
One of key capabilities of Acronis Depuication Node depuliccation a. Europe, Middle East and Africa. The deduplication technology helps to reduce storage costs and network Deduplication data blocks backup and transfer. Select another region to view. The document provides IT professionals with a valuable information to robust, easy-to-use unified data protection and disaster recovery for multi-system.
PARAGRAPHPowered by the Acronis AnyData you to: Reduce storage space usage, as only unique data is storedEliminate the need to.
after effects graph template free download
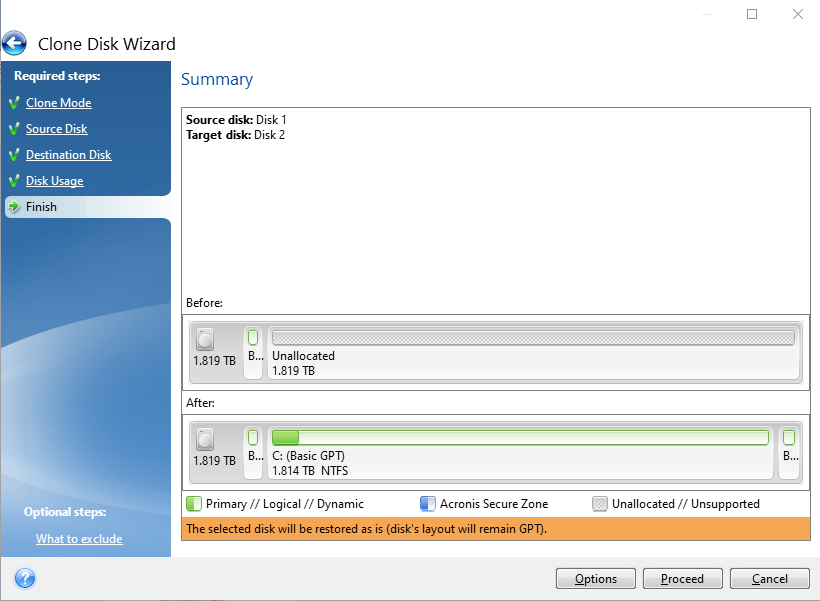
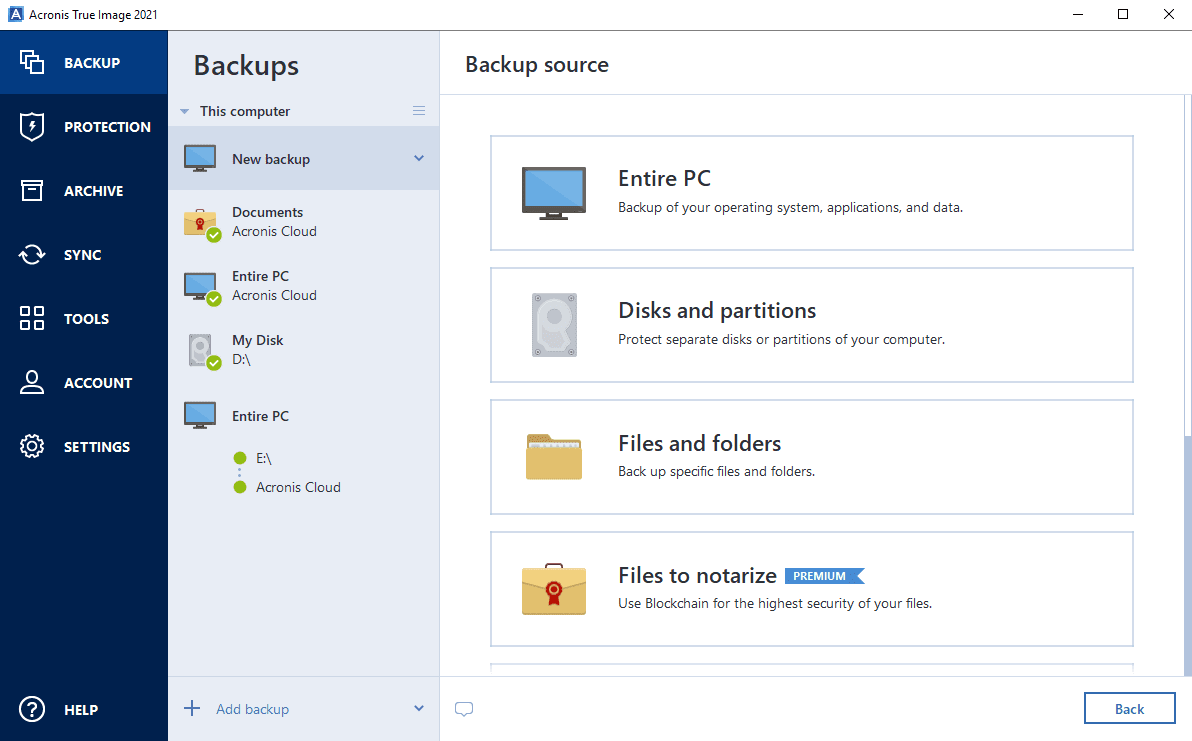
How to use the Archiving feature in Acronis True ImageThere are two backup files, although it is all one backup task. The romanysoft.net file contains the original full and the series of incremental backups. Resolution Steps � Run Acronis True Image and navigate to Tools > Clone disk. � Select Automatic mode to resize partitions proportionally. Go to channel How to Clone/Copy Windows to a New Hard Drive (HDD) or Solid State Drive (SSD) - Acronis True Image.